We take a look at two recently published reports on the current state of cybersecurity.
Last June, a couple of interesting reports were published that shed light on the current state of cybersecurity. The first is Sophos’ State of Ransomware 2025, which analyzes the causes and consequences of ransomware for organizations targeted by these attacks. Secondly, we will take a look at Bitdefender’s Cybersecurity Assessment Report, which provides insight into how IT and cybersecurity professionals view organizations’ preparedness against current risks, with some very interesting conclusions.
Contenidos
Ransomware attacks: Causes and Consequences
The Sophos report surveyed 3,400 IT and cybersecurity professionals from 17 countries (Australia, Brazil, Chile, Colombia, France, Germany, India, Italy, Japan, Mexico, Singapore, South Africa, Spain, Switzerland, United Arab Emirates, United Kingdom, and the United States) about their experience as victims of ransomware attacks. It provides very interesting data on organizational challenges and threats, but particularly highlights the areas where organizations still have work to do and where they are failing.
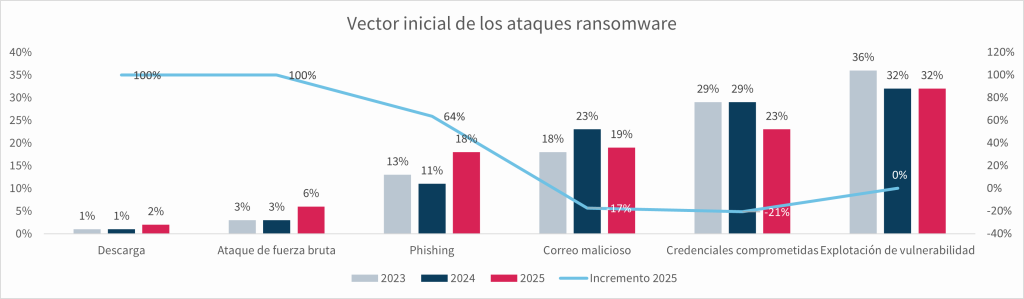
Fraudulent emails are the primary initial vector
The main cause identified by participants is exploitation of vulnerabilities (32%), followed by compromised credentials (23%). However, phishing (18%) and malicious emails (19%) together account for 37%, making fraud the primary entry point for ransomware attacks.
Additionally, unlike the other leading causes (which have remained the same or decreased), phishing as the origin of ransomware attacks has grown significantly compared to 2024: 64%.
Both phishing and malicious emails rely on deceiving recipients, whether through brand impersonation, person impersonation, or false information (such as fake promotions or fraudulent procedures), to obtain sensitive data directly or distribute malware. All of this falls under online fraud.
It is worth noting the Global Incident Response Report 2025 by Palo Alto Networks, which confirms the significance of phishing and emphasizes the role of social engineering. This helps explain the prominence and increase of online fraud as a primary entry point for cyberattacks:
In Spain, the main initial vectors are exploitation of vulnerabilities (30%), compromised credentials (21%), and malicious emails (17%).
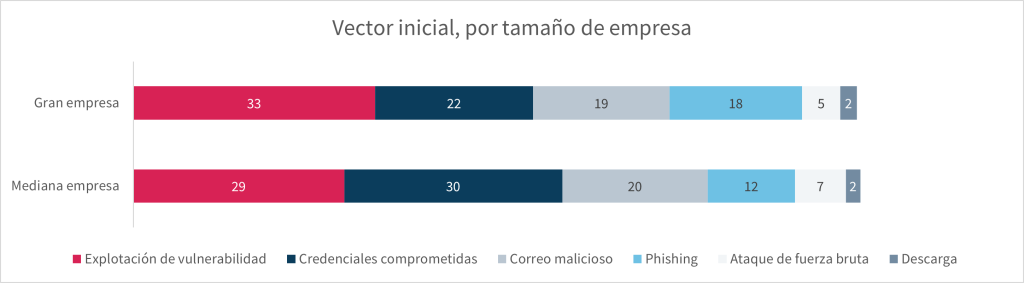
Differences between medium and large companies
In general terms, there are no substantial differences between medium and large companies. In both cases, exploitation of vulnerabilities is the main initial vector for ransomware attacks, closely followed by fraudulent emails when combining phishing and malicious emails.
However, examining the data highlights the following:
-
Large companies are more targeted by fraudulent campaigns. Online fraud as a cause is more prominent in large companies, with a 5-point difference (32% for medium companies vs. 37% for large companies).
-
Large companies experience more phishing. This difference is primarily due to phishing, which shows a 6-point gap between medium (12%) and large companies (18%).
-
Medium companies need to improve credential security. At 30%, compromised credentials as the main cause of ransomware attacks exceed exploitation of vulnerabilities by 1 point, which remains the main cause for large companies (33%).
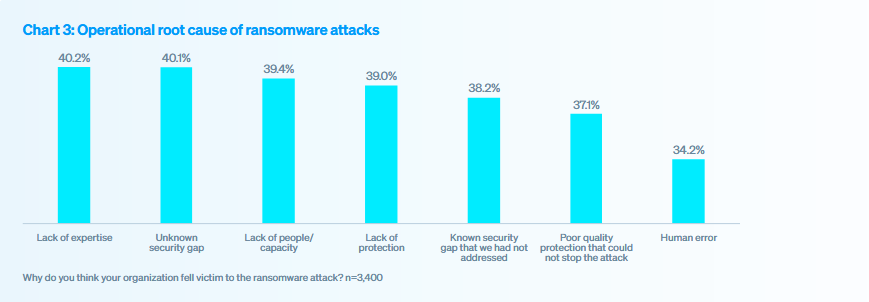
Causes: 2.7 factors impact company security
When asked, “Why do you think your organization has been a victim of a ransomware attack?”, participants selected an average of 2.7 factors that exposed the company. The most cited were lack of expertise and an unknown security gap. However, all possible responses were fairly evenly distributed, so no single factor stands out significantly.
In Spain, the main factor mentioned by participants is unresolved known security gaps (42%), followed by lack of personnel or capacity (41%).
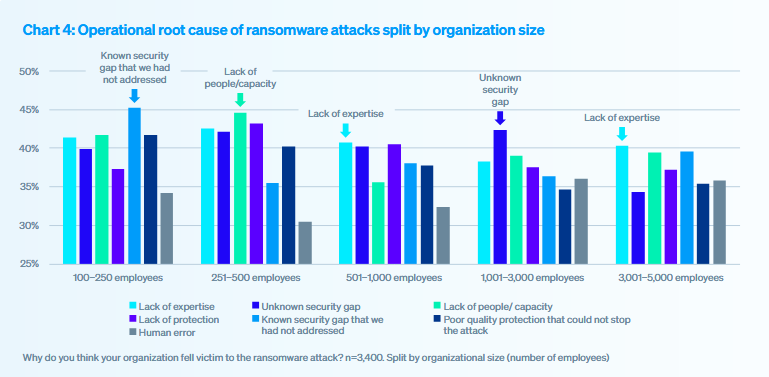
Different size, different factors
Where we find differences of more than 10 points between security risk factors is when looking at company size. Although the study differentiates five segments—one at the high end of medium-sized companies and the rest across various large company ranges—observing the differences between them is interesting. Here’s what stands out:
-
Medium-sized companies (100 to 250 employees): Except for human error and lack of protection, mostly resolved issues with less impact, the challenge is fairly evenly distributed across the remaining factors, namely knowledge and resources. The main risk factor for this group is unresolved known security gaps.
-
Large companies up to 500 employees: Similar to the previous segment, risk factors are based on knowledge and resources, but with two differences: the primary factor is lack of personnel or capacity, and lack of protection increases.
-
Large companies, 501 to 1,000 employees: In this segment, vulnerability is more evenly distributed across all factors, including an increase in human error. Unlike other segments, lack of personnel or capacity decreases.
-
Large companies, 1,001 to 3,000 employees: The trend is similar to the previous segment, but unawareness of security gaps increases as a risk factor.
-
Large companies, 3,001 to 5,000 employees: In this segment, several factors rise above others again: lack of experience, lack of personnel or capacity, and unresolved known security gaps.
In short, as companies grow, lack of capacity and resources is addressed, but when they reach a considerable size, knowledge and available resources become a problem again.
Sectors with key risk factors
Although, in general, vulnerabilities are fairly evenly distributed among the factors mentioned in the report, sector-specific data show that some industries face higher-risk factors.
For example, Higher Education companies show a spike (49%) in the factor unknown security breaches, which is 9 points above the average. The Professional Services & Business and Retail sectors also show increases, though to a lesser extent, both 6 points above average (46%), as does the Finance sector (44%, 4 points above average).
The Finance sector also spikes at 44% (5 points above average) in the factor lack of protection, which is alarming given it is one of the most targeted sectors for fraud campaigns.
The State Public Administration sector stands out with an increase of 7 points above average (45%) in the factor unresolved known security breaches, also concerning as it is another frequently targeted sector.
Other notable risk factors in commonly targeted sectors include:
-
Energy & Utilities: lack of expertise (43%, 3 points above average)
-
Industry: lack of expertise (42%, 2 points above average)
-
Healthcare: lack of personnel or capacity (42%, 2.5 points above average)
-
Technology & Telecommunications: unresolved known security breaches (42%, 4 points above average)
-
Distribution & Transport: very poor protection (41%, 4 points above average)
Cybercriminals lose 50%: from $2 million to $1 million per payment
44% of ransomware attacks are stopped in time
Despite the risk factors, almost half (44%) of ransomware attacks are stopped in time, representing a 63% increase compared to 2024 and the best figure in the last 6 years.
Conversely, 50% of ransomware attacks result in data encryption, a 28% decrease from 2024, and in 6% of cases, data was not encrypted but extortion still occurred. In Spain, 47% of attacks involved data encryption, 3 points below the 2024 average (50%) and a 39-point improvement compared to 2024, when 89% of attacks ended with data encryption.
In 14% of attacks, cybercriminals managed to steal data. This rises to 28% in cases where data was encrypted. In Spain, cases where data was both encrypted and stolen reached 36%, 2 points higher than in 2024 (34%).
Looking at the data by company size provides insights for pattern recognition:
-
The smaller the company, the lower the probability of data encryption and theft in ransomware attacks, though this may be due more to an inability to detect data theft.
-
The larger the company, the lower the probability of being extorted without data encryption.
-
The larger the company, the lower the ability to stop ransomware attacks
However, the large company segment of 1,001–3,000 employeesis an exception: it has a higher ability to stop attacks and, among large companies, suffers the least data theft. This may be because this segment enjoys the advantages of being a large company (resources) without the disadvantages of larger companies, such as organizational complexity.
49% of organizations pay a ransom
97% of participating organizations report having recovered their encrypted data. Of these, 54% recovered data through backups, while 49% paid a ransom. This is the first time in the past six years that this figure has started to decline, down 7 points from 56% in 2024.
In Spain, this decline is more pronounced, dropping from 56% in 2024 to 36% in 2025. However, the percentage of organizations that paid a ransom rises to 70% (16 points above the global average), although it has decreased 3 points from 73% in 2024.
What do cybercriminals demand and how much do organizations pay?
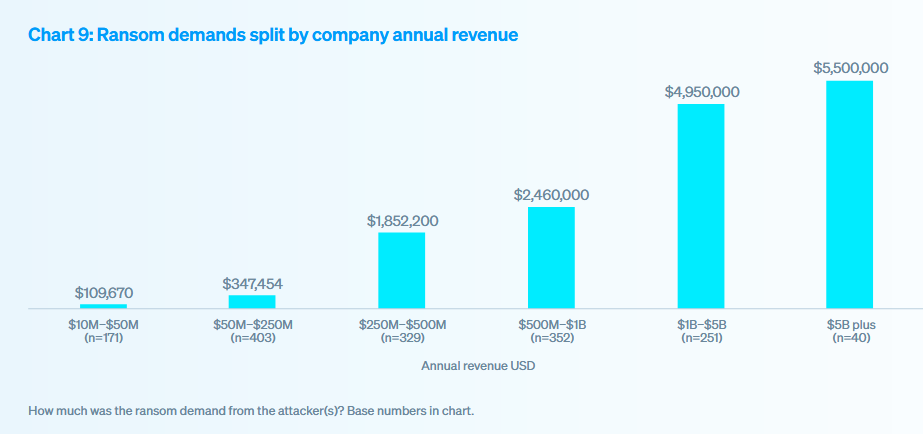
Although the median ransom demand in 2025 was $1.3 million, this figure varies significantly depending on the organization’s size: the higher the revenue, the higher the amount demanded. For example, medium-sized companies face demands of just over $100,000, while large companies can be asked for more than $5.5 million.
The median cost per payment has decreased from $2 million in 2024 to $1 million in 2025. This decline results from a reduction in payments of $5 million or more, as well as a general decrease in ransom payments overall.
However, on average, 85% of the demanded amount was paid. This means that most ransomware victims paid less than what was demanded (53%). On average, two factors contributed to this reduction, mainly negotiation and external pressure (media or legal). Other key factors included reduced incentives, early-payment “discounts,” or negotiations through third parties.
Although a minority, in 18% of cases organizations ended up paying more than demanded. On average, two factors were involved, notably: cybercriminals believed the company could pay more, and the organization was identified as a high-value target. Other determining factors included attacker frustration, backup failures, or delays in payment.
In general, although larger companies face higher demands, the gap between the amount demanded and paid is also greater, indicating more capacity to negotiate or reduce the ransom.
In Spain, the median amount demanded is $912,000, while the median paid is $322,500, reflecting a positive trend. In 2024, the median in this same survey was $4.4 million. On average, organizations paid 80% of the demanded amount (no cases exceeded the demand), 5 points below the global average (85%), and only 50% of ransom demands exceeded $1 million, compared to 73% in 2024.
Recovering from a ransomware attack costs $1.53 million and takes between one week and one month
Although this is a considerable figure, it represents a 44% decrease compared to 2024. Again, the average varies by company size, being around $640,000 for medium-sized companies and over $1.8 million for larger companies.
In Spain, the average cost of recovery after a ransomware attack is $1.15 million, according to the report.
Regarding recovery time, most respondents (37%) report 1 week, followed by up to 1 month (28%). This has been the predominant trend in the last four years of the survey, with the exception of 2024, when 1 month slightly surpassed 1 week (30% vs. 28%).
Notably, in 2025, the percentage of same-day recoveries doubled, while recoveries taking 1–3 months or 3–6 months decreased by 41% and 75%, respectively.
Overall, organizations have managed to accelerate recovery times following ransomware attacks.
Personal and Professional Consequences
The survey also considered the personal consequences for participating employees as well as organizational changes resulting from attacks. It includes positive, neutral, and negative aspects, with anxiety, stress, pressure, workload, and organizational changes being the main consequences:
41% Increased anxiety or stress about future attacks
40% Greater pressure from senior leaders
38% Continuous increase in workload
34% Feelings of guilt for not having stopped the attack
38% Change in team priorities/focus
37% Changes in team/organizational structure
25% Our team leadership was replaced
31% Greater recognition of senior leaders
31% Staff absence due to stress/mental health issues
Cybersecurity Health and Challenges: What Professionals Say
The Bitdefender report surveyed 1,200 IT and cybersecurity professionals across six countries: the United States, Singapore, Italy, Germany, the United Kingdom, and France. It provides insightful data from the perspective of professionals who fight and experience cybercrime daily while protecting their organizations. Let’s take a closer look at the data.
The Rise of LOTL Techniques Sets New Priorities
68% of surveyed professionals agree with the report that reducing the attack surface by disabling unnecessary tools or applications is a necessity. According to Bitdefender, this is due to the rise of LOTL techniques, which exploit existing tools in the environment.
For this purpose, the main challenges highlighted by professionals are balancing security and usability, and integrating legacy systems with modern infrastructure.
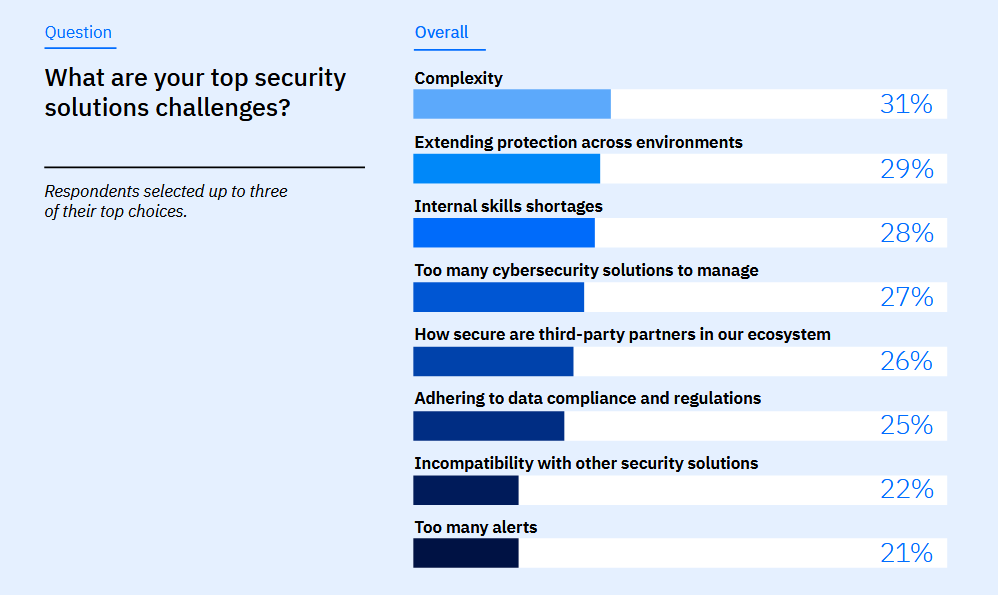
Complexity: The Main Challenge for 1 in 3 Professionals
In general, the main challenge for participating IT and cybersecurity professionals is the complexity of the environments they manage, which often leads to alert fatigue (mental exhaustion from handling a large number of alerts, many of which are low priority, false positives, or executable).
Additionally, 1 in 4 respondents identifies the growing regulatory framework and data compliance as a major challenge in securing their environments.
Other notable challenges highlighted by participants include the lack of internal security skills to fully leverage solutions and extend capabilities across multiple environments.
Lack of Visibility and Automation
77% of respondents report not having enough insights into their environment. Additionally, 50% indicate that a lack of automation makes their work more difficult, and 49% state that the need for constant monitoring, combined with alert filtering, management, and real-time response, has led to burnout symptoms.
AI: Driving a new arms race
The report highlights the advantages AI offers to both attackers and defenders, creating an arms race in adopting new AI-based measures to counter opponents.
So, what do professionals think? 51% of participants consider AI-driven threats their top concern, with AI-enhanced malware and social engineering identified as the main risks. In fact, 63% of respondents reported being cyberattacked using AI-involved techniques in the past 12 months, particularly in the United States and Singapore, with averages of 75% and 71%, respectively.
Disparity of Vision Between Roles: Confidence and Skills
When asked about confidence in their organization’s ability to manage risks amid a growing attack surface, the greatest disparity appears between senior executives and mid-level managers. Senior executives are the most confident, with 45% reporting they feel very confident, compared to only 19% of mid-level managers at the same confidence level.
There is also a mismatch regarding priorities. Senior executives point to adopting AI tools for advanced threat detection, while mid-level managers prioritize strengthening cloud security and identity management. This disparity highlights an important point: while some focus on innovation, others are caught up in day-to-day operations.
Although with some differences, both groups confirm that their organizations suffer from a skills gap that has worsened over the past 12 months (57% and 40%, respectively).
Fraud, the biggest threat in 2025
Fraud, specifically attacks using BEC (Business Email Compromise) and targeted phishing is considered the greatest threat by both senior executives and mid-level managers, with 44% in both groups.
Keeping silent, increasing
When asked whether they were instructed not to report attacks to authorities, the figures show a significant increase since 2023, rising from 42% of participants to 58% in 2025. This figure drops considerably in European Union countries, averaging 45%, under the strict GDPR regulatory framework. In the United States and Singapore, the results are 74% and 76%, respectively.
Do you need help against online fraud?
Write to us with your inquiry, and we will get in touch with you soon.
