In this new installment of the Brand Protection 101 series, we take a look at the fraud techniques that brands suffer from to understand what they’re up against and how to deal with it.
Contents:
To properly protect our brand, it’s essential to know what we’re up against. In this article, we review the main online fraud threats and techniques that brands face.
Fraud main goals
Generally, when a cybercriminal carries out a fraudulent attack, they don’t do so against a brand, that is, to damage its reputation, but rather, the brand as a means of obtaining economic benefit.
Thus, the reputational damage a brand faces, as well as economic losses (fines, compensation, lost sales, etc.), are collateral damage.
The offender's strategies
To obtain this financial gain, cybercriminals use different strategies (with a very fine line between them):
- Phishing: They impersonate the brand using various deceptive techniques (which we will discuss later). This makes the victim believe they are interacting with the legitimate brand.
- Confusion: They use techniques that create confusion in users so that, without actually imitating or impersonating the brand, they believe they are interacting with it.
- Exploitation of notoriety: They use the brand or well-known figures to indirectly generate income, such as online advertising.
In the first two cases, the objective is to obtain sensitive data (such as login credentials, card numbers, ID, etc.) with which to access credit (bank accounts, online payment methods), or payments and transfers directly from the defrauded users.
Main online fraud techniques
Next, we’ll look at the techniques cybercriminals use to trick users into thinking their interaction with the brand is legitimate.
Cyberquatting
This term refers to the registration of domain names with fraudulent or speculative intent. In other words, when a third party registers a domain name containing the trademark.
Cybersquatting can occur at two levels:
- In the domain name: when the domain name contains the trademark.
- In the domain extension: when a domain name identical to the trademark is registered, with a TLD not registered by the trademark.

Let’s see it in examples:
Example 1
A third party registers a domain name containing your brand with the aim of selling it to you and thus making a financial profit.
They often use less widely used domain extensions that brands don’t register:
yourbrand.company
yourbrand.online
yourbrand.shop
Example 2
A third party registers a domain name that is an exact match or contains your brand to trick your users, customers, and suppliers into believing it is a legitimate link in phishing attacks.
They often use phrases that can appear legitimate if you don’t pay attention:
yourbrand.company
yourbrand.online
yourbrand.shop
If you’d like to learn more, we recommend reading our article on cybersquatting, or you can download our quick guides in PDF format from Linkedin:
Within cybersquatting, there are more subtle and widely used deceptive tactics for domain name-related phishing and scamming campaigns:
Typosquatting
This involves the deliberate use of typos in the domain name so that the user, at a quick glance, doesn’t realize it’s a fraudulent domain.
Examples: gogle.com, amazpn.es…
Confusing characters
In this case, different characters are used that visually resemble the originals.
Examples: amaz0n.es, arnazon.es…
Homoglyphs
In these cases, homoglyphs are used, characters from different writing systems that are visually identical or very similar.
Examples: tumarca.com (with a Cyrillic “a”), amazΟn.es (the “o” is the Greek ómicron), z00m.es (the “o”s are zeros)…
Domain hijacking
While cybersquatting refers to the registration of domains that the brand has not registered, other techniques allow brands to steal access to legitimate domains.
Sitting Duck attacks
The Sitting Duck tactic, which refers to the vulnerability of a duck sitting, involves gaining access to the DNS settings of a legitimate brand domain by exploiting vulnerabilities in DNS management.
Once access is gained, cybercriminals make the necessary modifications so that the domain resolves to a fraudulent website.
What are these vulnerabilities?
- Authoritative DNS services delegated to a provider other than the domain registrar.
- The registry’s authoritative name servers cannot resolve queries.
- Exploitation of human error in authoritative DNS providers (the provider is tricked into providing data or making configuration changes).
If you want to learn more about Sitting Duck attacks and how to prevent them, read our dedicated article on this topic.
DNS Dangling attacks
Unlike Sitting Duck attacks, DNS Dangling attacks don’t take control of the DNS, but rather of the cloud services they point to.
Cybercriminals detect domains or subdomains that point to expired or deleted cloud services. They create services with the same name, so that the DNS again points to the same, now active and fraudulent service.
- More credible phishing campaigns.
- Malware distribution campaigns with legitimate links.
- Unauthorized access to sensitive data.
If you want to see examples and how to prevent these attacks, we recommend reading our article dedicated to DNS Dangling attacks.
In both cases, these are situations of extreme risk, as the assets they gain access to are legitimate in the eyes of the user and fraud filters. Furthermore, since these are forgotten assets, by the time brands realize the problem, it’s already too late.
Web site cloning
Website cloning, as indicated, consists of making a copy of a legitimate website. This includes code, images, text, look and feel, etc. It tricks the user into leaving their credentials or other sensitive data, such as a credit card, under the impression that they are making a legitimate reservation or purchase.
These are almost identical copies, as there are often small details, such as links, that cybercriminals don’t modify and that can help us identify a fraudulent website.
Currently, it is very easy to clone a website, which is why cybercriminals sell them in phishing packages on the Dark Web.
A cloned website does not necessarily have to be hosted on a domain that is occupied, meaning it doesn’t have to mention the brand. If this is the case, ICANN’s recovery mechanisms can disable the content and block the domain.
In the case of domains that don’t mention the brand, the matter becomes more complicated, but there are solutions that allow us to detect these cases.
Obviously, a cloned page poses a very high risk to users, since they are interacting with the brand before their eyes, and only the most suspicious will avoid falling into the trap.
Learn more about this topic and learn how to prevent these types of scams by reading our article on the subject.
Fraudulent web content
Whether the domain is cybersquatting or not, the content displayed on it may be cybersquatting or represent a trademark infringement. For example:
- Mentions intended to cause reputational damage.
- Mentions of the trademark for the purpose of exploiting its reputation.
- Mentions of the trademark as a claim to sell counterfeits, copies, or similar products unrelated to the brand.
- Use of the logo or protected images.
- Use of the brand’s look and feel that may cause user confusion.
- …
A Cease & Desist request is made to stop the fraudulent or infringing activity on the domain. The greatest difficulty lies in the detection and analysis of cases, which requires legal expertise to determine the nature of the infringement and how to act.
Phishing
The well-known phishing technique consists of sending emails with a lure (whether fraudulent or not) intended to trick the user into sharing sensitive data.
Very often, phishing is used in a brand impersonation campaign and is accompanied by other techniques such as website cloning. We come across news about it every day, such as the recent impersonation campaign by the Treasury.
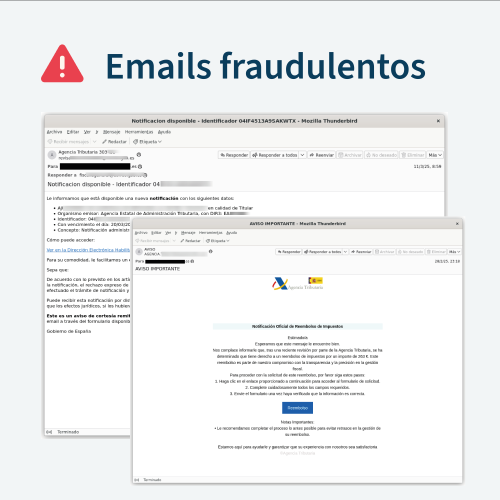
Other times, phishing scams use current events or product hype to carry out phishing attacks without impersonating a brand. A clear example is this data theft campaign that took advantage of the Oscars 2025 hype:
They are also very common during massive sales campaigns such as Black Friday, during which fraud increases: up to 150% in 2025.
Smishing and Whatsapp
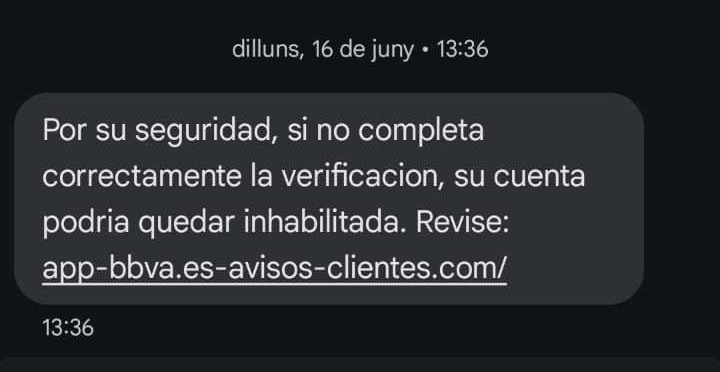
Smishing is the SMS version of phishing: messages in which we receive a link to a fraudulent domain that captures users’ sensitive data. Cybercriminals often use urgency and fear to confuse users and thus gain access to bank accounts or credit card numbers, for example.
We often see it impersonating banks or public agencies, always in connection with lost money or unauthorized access, pending payments, canceled accounts… all of which are fake, of course.
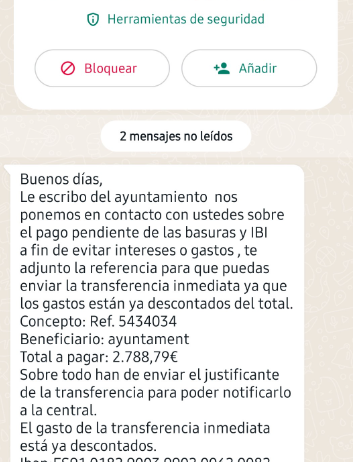
Since last year, WhatsApp has become another platform for sending fraudulent messages through chats that impersonate organizations. Multiple city councils have been targeted in recent months, and the scheme is the same: payment is requested for an outstanding invoice or tax.
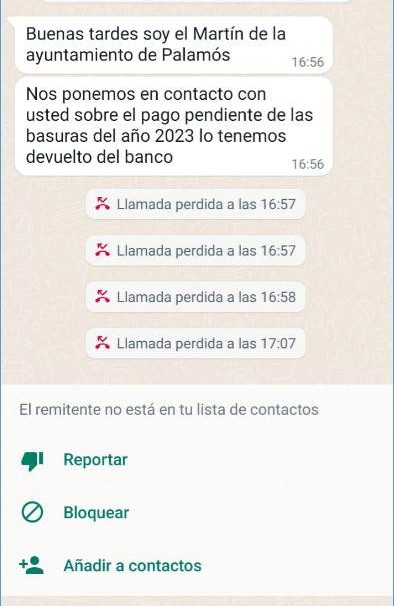
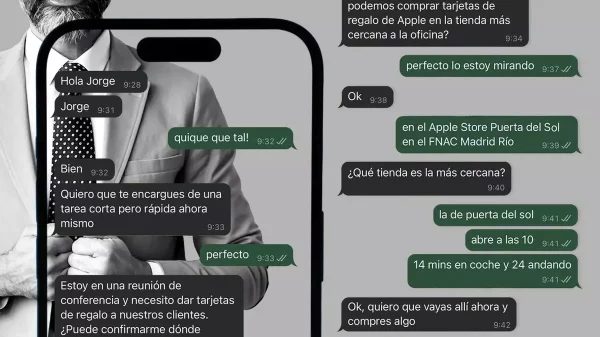
Another practice is the incorporation of users (without their consent) into fake WhatsApp groups that may use brands as a lure, and in which messages with fraudulent links are shared.
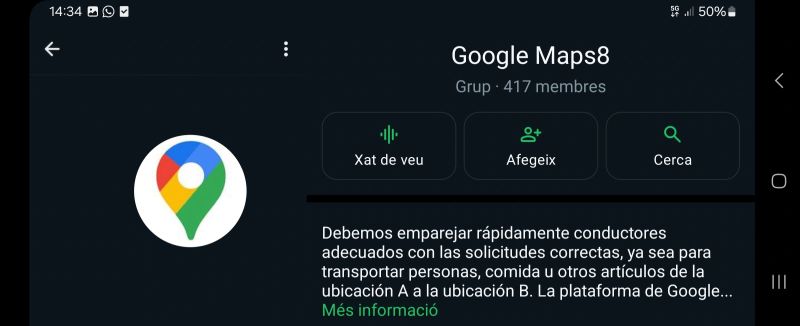
A new phenomenon we’ve seen in recent months is the so-called intern attack, which is highly targeted, as it targets new hires in brands’ financial teams, capable of making payments and transfers, by impersonating a manager or executive. In short, it’s the WhatsApp version of a BEC attack.
Vishing and call spoofing
Vishing follows the same mechanics: brand impersonation through an urgent message requesting payment, but the medium is a voice call. This technique is primarily used to impersonate financial institutions and its objective is to obtain users’ bank account login details.
Occasionally, especially in cases of financial institution impersonation, it is accompanied by phone spoofing, or the concealment of an illicit phone number behind a legitimate one.
We recently saw the Tríodos case in which a bank customer received a call from her bank (she saw the legitimate phone number through spoofing) and during the call, under the pretext that her account was the target of a fraudulent attack, she gave up the verification code to access it.
Email spoofing and spear phishing
In this version of spoofing, the deception is carried out via email. Email spoofing encompasses other techniques, such as phishing, the use of typosquatting domains, content that imitates the brand’s look and feel, and the goal is the same: to deceive the user by imitating another brand to obtain sensitive data or payments from fraudulent recipients.
Unlike other techniques, email spoofing alters the “From” address of emails, masking a fake email with a legitimate name and compromising the SMTP protocol.
Brands are not only victims of impersonation, but are also targets of this type of attack with spear phishing campaigns: targeted attacks with personalized messages about specific targets, such as employees or managers.
To detect these cases, DMARC can be helpful. You can learn more by reading our article on email spoofing.
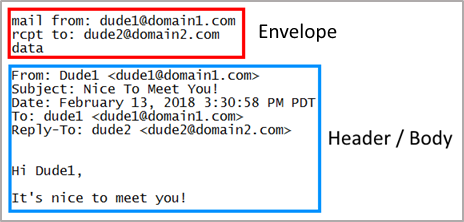
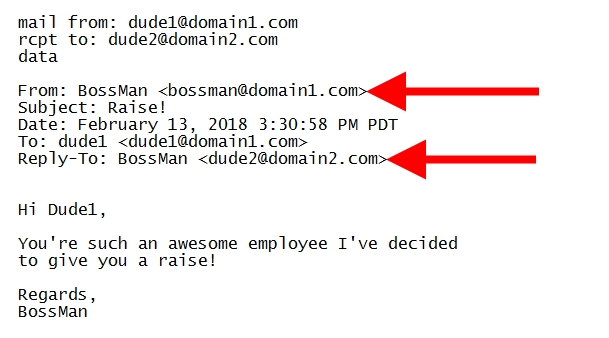
Source: proofpoint.com
Fraudulent ads and comments
In the eCommerce space, brands are frequently victims of fraudulent ads, products, and comments on various online sales channels, such as social media, eCommerce sites, and marketplaces.
The purpose of this fraudulent content is to sell counterfeits and copies of the brand’s products, but it is also common to use the brand as a marketing tool to sell other products or legitimate products on the gray market (outside of the brand’s authorized distribution channels), often at lower prices.
Brands also deal with fraudulent comments, for example, in legitimate content advertising or commenting on the brand, which links to fraudulent pages, counterfeits, etc.
Brands that suffer these types of violations must implement monitoring solutions to detect and eliminate them quickly. This technology is easy to implement today, and it has advanced significantly (and will continue to do so thanks to AI).
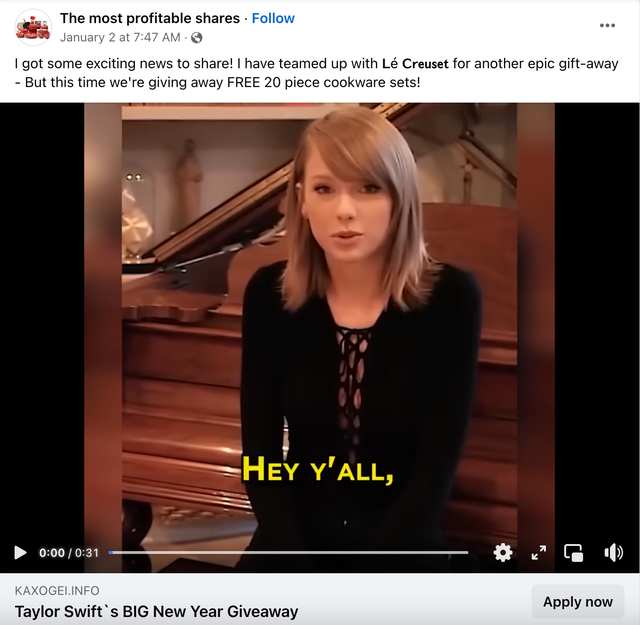
Another trend that has been on the rise in recent months has been the exploitation of the image of celebrities and well-known figures, especially experts on specific topics. This can affect brands that have gurus on their team or that use influencers or celebrities in their advertising campaigns, as these campaigns can be diluted or even delegitimized by these parallel illicit campaigns.
Fake profiles on Social Media
Once again, we encounter cases of impersonation or imitation of legitimate brand profiles. Generally, the objective remains financial: stealing traffic from legitimate profiles, sharing fraudulent links, etc..
Brands should not confuse parody, fan, or hater profiles. Comments, even unfavorable ones, are legal as long as they do not constitute a trademark infringement or abuse, that is, the brand is used to cause harm.
Fraudulent apps
Apps that mimic legitimate financial institution apps are common, but also any widely used app (such as streaming platforms, games, etc.).
The objective is financial, either through the theft of credentials to gain access to bank accounts or card numbers to make payments, but also through the theft of other sensitive data to be sold on the Dark Web.
Apps that do not phish can obtain this data through malware distribution, that is, by infecting our phones.
Other apps will generate revenue simply through advertising or traffic to illicit websites.

Brand Protection 101 series
Need help against online fraud?
Contact us, we'll get back to you shortly.